Warning to 1,800,000,000 Gmail users over sophisticated scam
2025-05-23 HaiPress

Don’t let someone else get their hands on your gmail account (Picture: Getty)
Gmail users have been warned about a highly convincing scam email thatappears to come from Google themselves.
The email seems to come from no-reply@accounts.google.com,which is the address that real security updates come from.
It links to a webpage hosted by Google,too,which is another convincing sign.
But the website was not made by them; it was made by scammers trying to trick you.
The email claims that ‘a subpoena was served on Google LLC requiring us to produce a copy of your Google Account content’.
It links to a sites.google.com domain designed to look like Google’s genuine support page.
However,the real support webpage is on accounts.google.com,while the ‘sites’ domain is one that anyone can build a free webpage on.
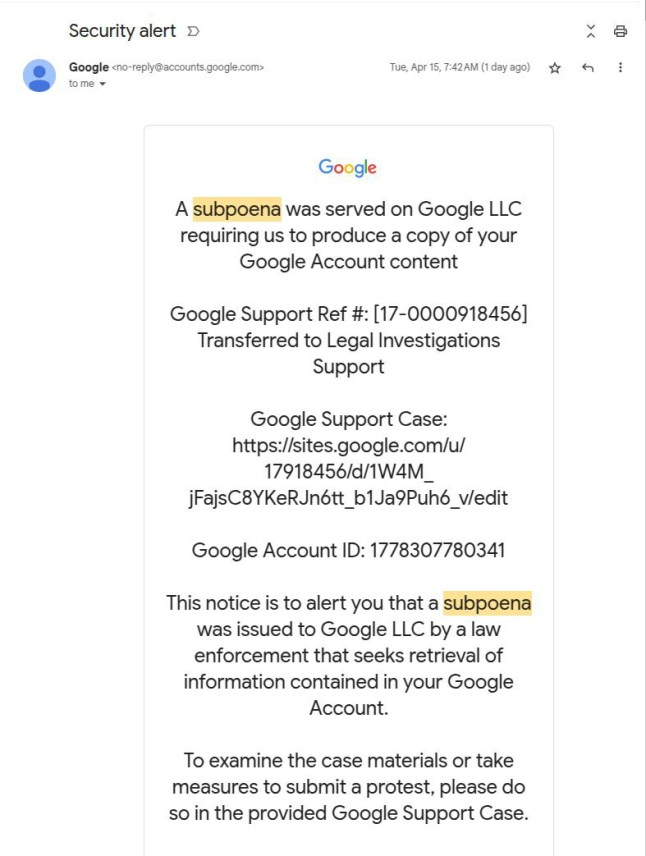
The scam email which appeared to be sent by Google (Picture: @nicksdjohnson/X)
Ordinary users are unlikely to know or notice this,however,and could inadvertently grant scammers permissions that could allow them access,or target you with malware.
Security software firm Kaspersky said that there are other clues,too.
If you look closer at the email details,the to and mailed-by fields contain a jumble of letters of emails which have nothing to do with Google,showing me[@]googl-mail-smtp-out-198-142-125-38-prod[.]net and
fwd-04-1.fwd.privateemail[.]com.
The scam was first revealed by tech developer Nick Johnson.
How could they make it so convincing?
The scammers used Google OAuth technology,which is what you see when you use your Google details to sign into a different app.
Those who fell victim to the scam approved the permissions thinking they were giving Google themselves permission.
It is not clear exactly what the scammers hoped to achieve by this,but could involve data theft or infecting the victim with malware.
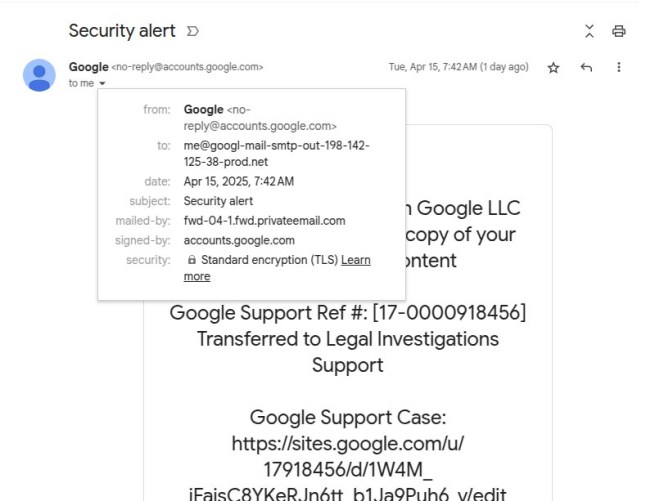
The ‘from’ field looks legit,but not the ‘to’ or ‘mailed-by’ (Picture: @nicksdjohnson/X)
Kapersky said that when an OAuth app is registered,‘the web application administrator can manually enter completely arbitrary text in the App
Name field – this is what the criminals apparently took advantage of.’
The mechanism that attackers used to do this has now been shut down,which will prevent this method of attack from working in future.
A Google spokesperson said: ‘We’re aware of this class of targeted attack from this threat actor and have rolled out protections to shut down this avenue for abuse.
‘In the meantime,we encourage users to adopt two-factor authentication and passkeys,which provide strong protection against these kinds of phishing campaigns.’
They recently issued guidance on spotting scams,saying they will not ask for any of your account credentials,including your password,one-time passwords,confirm push notifications,and will not call you.
